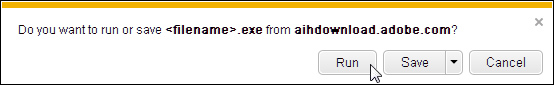
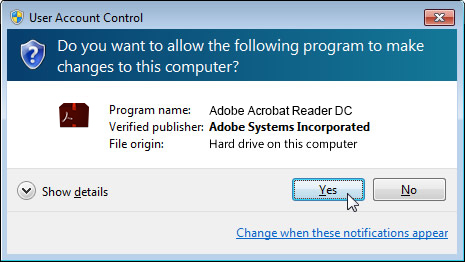
[[f9.sad]]
[[f9.angry]]
[[f9.sleepy]]
[[f9.shock]]
[[f9.kiss]]
[[f9.inlove]]
[[f9.pizza]]
[[f9.coffee]]
[[f9.rain]]
[[f9.bomb]]
[[f9.sun]]
[[f9.heart]]
[[f9.heartbreak]]
[[f9.doctor]]
[[f9.ghost]]
[[f9.brb]]
[[f9.wine]]
[[f9.gift]]
[[f9.adore]]
[[f9.angel]]
[[f9.baloons]]
[[f9.bowl]]
[[f9.cake]]
[[f9.callme]]
[[f9.clap]]
[[f9.confused]]
[[f9.curllip]]
[[f9.devilface]]
[[f9.lying]]
[[f9.rofl]]
[[f9.billiard]]
[[f9.cakepiece]]
[[f9.rosedown]]
[[f9.shutmouth]]
[[f9.shy]]
[[f9.silly]]
[[f9.tongue1]]
[[f9.fastfood]]
[[f9.ring]]
[[f9.plate]]
[[f9.candle]]
[[f9.party]]